
Navigating Mars with Rust: Helping the Rover See In Computer Vision
This blog explores how Rust enables computer vision on a Mars rover, overcoming hardware limits to deliver reliable obstacle detection and autonomous navigation.
7 entries tagged with #Rust

This blog explores how Rust enables computer vision on a Mars rover, overcoming hardware limits to deliver reliable obstacle detection and autonomous navigation.
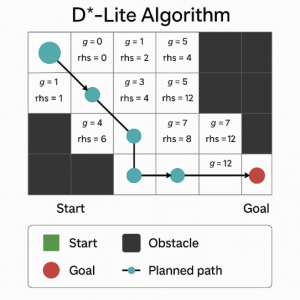
This blog showcases how Rust was used to implement the D*-Lite pathfinding algorithm for an autonomous Mars rover simulation. It highlights Rust’s strengths—such as memory safety, strong typing, and zero-cost abstractions—in building a responsive, efficient navigation system that adapts to dynamic obstacles.

We have taken our Ada Mars Rover demo, featuring a physical robot driven by formally verified SPARK software, to the next level by introducing a simulator that allows you to experience the Rover's capabilities virtually. This simulation, implemented in Rust, accurately models the Rover's movement in an obstacle-filled environment, all while being controlled by the original SPARK code. This project exemplifies the synergy between Ada and Rust, demonstrating how these technologies can be effectively combined to build reliable, safety-critical applications.
At AdaCore, we’re in the business of supporting people who develop high-integrity software, in particular for embedded systems. In terms of programming languages, this means supporting the most commonly found candidates, which in 2024 include C/C++, Ada/SPARK, and Rust. If you’ve already made your decision, we will support you. However, in a number of situations, people ask us: “What should we do? What’s the best out there?”. While it’s difficult to give a one-size-fits-all answer, there are some strategic elements to consider.
On June 25th, I attended the Rust Paris 2024 conference. Among around one hundred Rust enthusiasts and a program filled with captivating subjects and contributors, I presented (together with Thales) our vision for establishing a Rust ecosystem for certifiable embedded critical systems.
Informally, memory safety in a program means that each data access is well behaved; i.e., is consistent with the item’s data type, does not impinge on any storage locations beyond the data value’s boundaries, and, if the program is multithreaded, does not produce an inconsistent or corrupted value. Memory safety violations result in undefined behavior, which is a Bad Thing: instances like the notorious “buffer overrun” can turn an otherwise safe and secure program into a ticking virtual time bomb. Some of the most eventful malware attacks in recent years are due to memory safety violations, and the topic has moved from techno-geek subreddits into mainstream discourse. Anyone developing or acquiring software, especially for applications with high assurance requirements, needs to pay attention.
This blog post explains the concept of memory safety and the most common memory errors. Then, it introduces three memory-safe languages that have built-in countermeasures against memory errors.