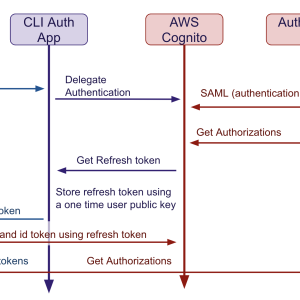
Identifying and authorizing users at AdaCore
Back in the 90s when AdaCore was founded, the state of IT security was very different. A unique Unix login and password were enough to connect to a shared server and run business applications. Most of the protocols used were still unencrypted, and the most elaborate access controls were based on Unix groups and perimeter defense. As the company evolved, we gave users access to more and more services, some not hosted on-premise. More services meant distinct credentials. Security-savvy users, who did not accept reusing the same password everywhere, had the burden of maintaining all these distinct credentials. Most credentials were long-lived, and very often shared. Also as the notion of perimeter defense became more and more fuzzy with the introduction of PaaS, IaaS, .. the need for safer access and communication protocols increased significantly.