
DNSSEC and DMARC Compliance at AdaCore
by Nicolas Venner –
DNSSEC
While foundational to the internet, the traditional DNS system has its vulnerabilities. Threats such as DNS spoofing and cache poisoning pose significant risks to the integrity and authenticity of DNS data. DNSSEC is designed to address this risk.
The first RFC for DNSSEC was published in 1997 to remediate such threats, and initial attempts to implement it started in 1999. However, scaling up proved impossible, and the standard was ultimately revised to become what it is now.
On the technical level, DNSSEC operates through key components, pun intended, including barbaric-sounding acronyms such as DNSKEY (DNSSEC public key), RRSIG (Resource Record Signature), NSEC (Next Secure Record), KSK (Key-Signing Key), and DS (Delegation Signer) records, creating a robust chain of trust.
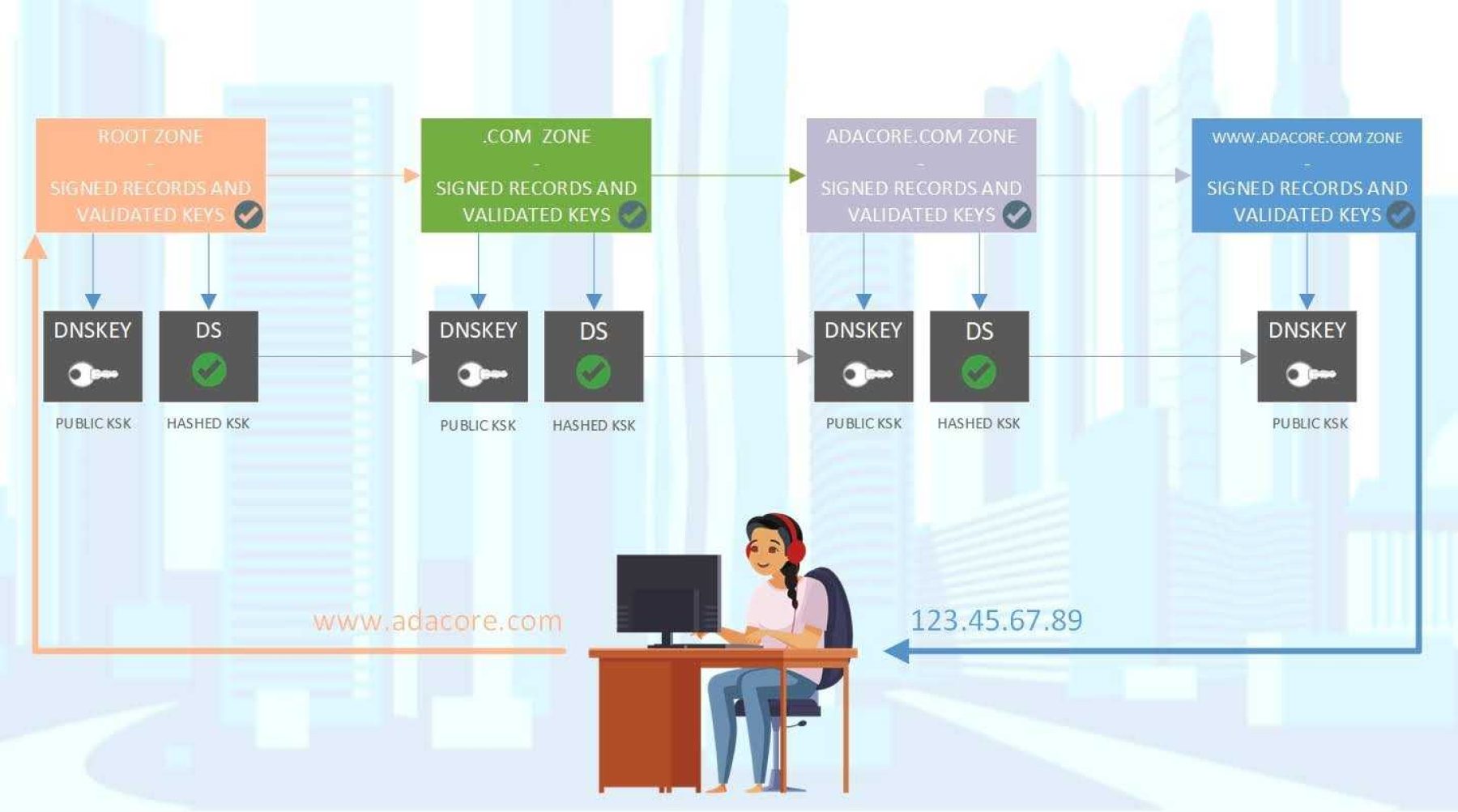
Ensuring the security of your request, from your local computer to the authoritative nameserver for the specified URL and back, involves a digital signature (or handshake) at each node. This mechanism guarantees that the content you intended to access is delivered and that the request remains immune to interception by unauthorized entities during transit.
Despite the standard being under development and deployment for over 25 years, the current global DNSSEC adoption rate server-side is meager: Verizon reports that by the end of 2023, the percentage of domains with valid DS records was 4.3% in .com and 5.3% in .net.
We're happy to announce that all our domains supporting the standard now have a valid DNSSEC offering.
DMARC
Expanding on initiatives initiated in 2010, a coalition of prominent organizations such as Comcast, Google, JPMorgan Chase, and Paypal joined forces in the spring of 2011 to develop a strategy for addressing fraudulent email on a large scale.
This effort encompassed two key aspects:
Facilitate senders in effortlessly disclosing policies for unauthenticated emails.
Empower receivers such as email providers to provide authentication reports to senders, aiding them in enhancing and overseeing their authentication infrastructure.
But what exactly is DMARC? This email authentication protocol builds on two existing protocols – SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail).
SPF allows the domain owner to specify which mail servers are authorized to send emails on behalf of their domain. DMARC leverages SPF by authenticating the "MAIL FROM" domain.
DKIM adds a digital signature to the email, allowing the recipient to verify that an authorized sender sent the message. DMARC uses DKIM to authenticate the "From" header domain.
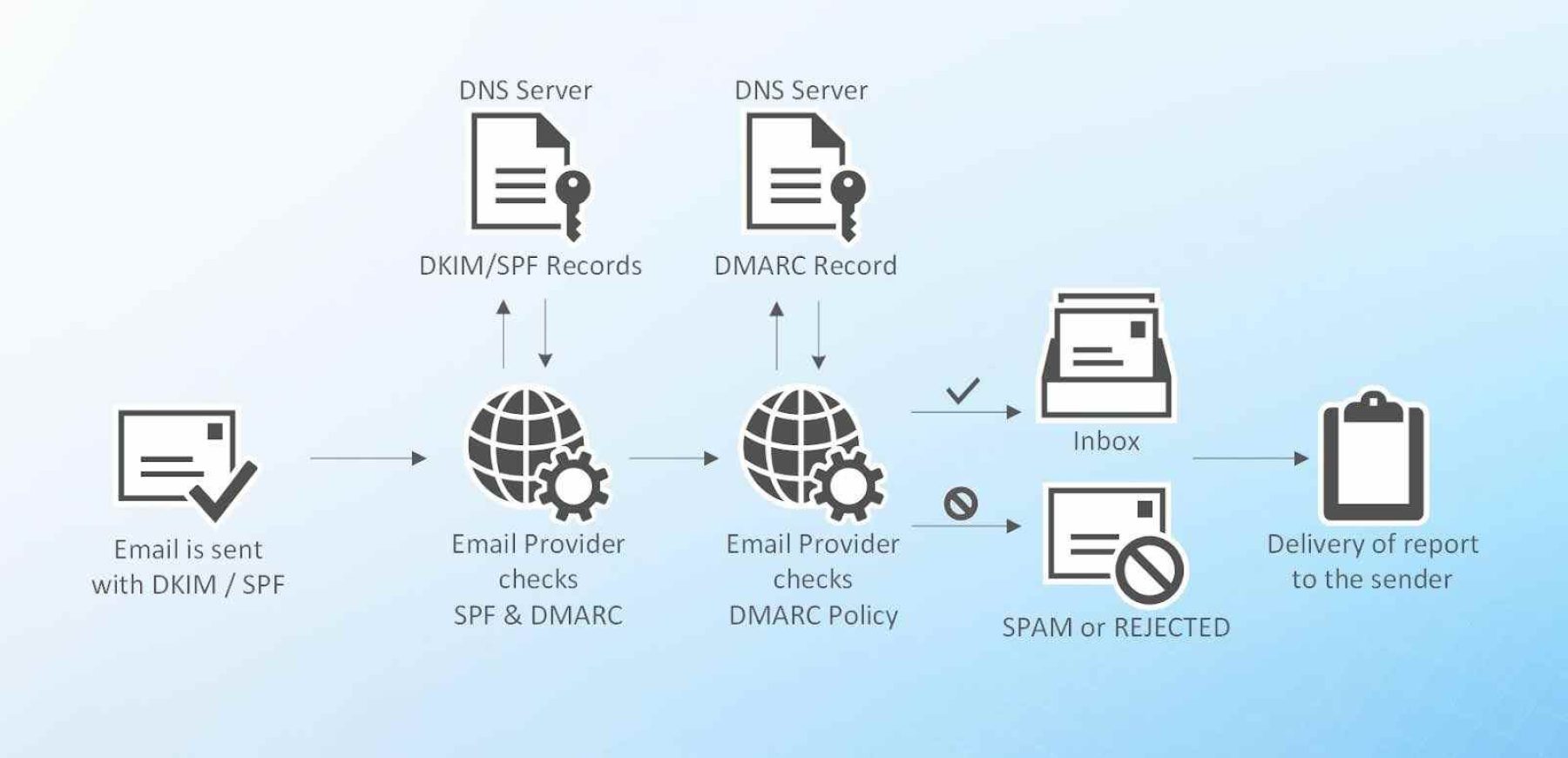
The standard helps reduce phishing attacks, improves deliverability by minimizing the chances of legitimate emails being marked as spam, and provides valuable insights through aggregate and failure reports.
However, as of 2023, only a third of the domains of the top 1000 global companies have a valid DMARC setup. Among these, more than half have their policy set to “none”, meaning no action would be taken server-side to stop suspicious emails, leaving recipients vulnerable to phishing attacks ( https://sendlayer.com/blog/dmarc-coverage-trends/ ).
We’re pleased to announce that all AdaCore domains now have a DMARC policy set to quarantine or reject, meaning that if you receive an email from us, you can rest assured we did send it.
